Security
How to Use Microsoft’s Cybersecurity Reference Architecture to Strengthen Security and Drive Profitability
| 5 min read
Security leaders face a fundamental challenge: they must protect users, data, and systems across multiple platforms, clouds, and devices — all without slowing down the business.
The Microsoft Cybersecurity Reference Architecture (MCRA)provides a structured way to meet that challenge. It maps every key security function, the technologies that support them, and the integrations that make them work together. Used effectively, it becomes more than a list of tools; it’s a strategic framework for improving security posture, reducing costs, and aligning IT and business priorities.
At The Partner Masters, we work with Microsoft partners to turn this framework into a clear, actionable roadmap for their customers — one that closes gaps, improves operations, and creates new opportunities for revenue growth.
Why the Reference Architecture Matters
Security conversations often occur in isolation: identity teams discuss authentication, endpoint teams focus on malware protection, and compliance teams concentrate on data classification. The reference architecture unites these elements into a single, cohesive strategy.
It provides:
- A complete view of Microsoft’s security capabilities, spanning identity, access, endpoint, cloud, and compliance.
- Clarity on how the components interact to strengthen defenses and streamline responses.
- A place for third-party tools and how they can be integrated effectively.
For partners, this approach enables a shift from product-focused discussions to a broader conversation about overall security posture and measurable outcomes.
Adapting the Architecture to the Real World
Most organizations run a mix of Microsoft and non-Microsoft tools. Identity can be managed through Okta, endpoint protection can be provided through SentinelOne, and VPN access can be secured through Cisco. The most effective approach is to tailor the architecture to reflect the customer’s current environment.
That process involves:
- Mapping the current state – Document the products and services in place today.
- Finding overlaps – Identify where functionality is duplicated, often at unnecessary expense.
- Designing the future state – Show where Microsoft solutions could replace, integrate with, or complement existing investments.
The result is a clear picture of where the organization stands today and a logical path toward an improved security posture.
Connecting Security to the Business Conversation
Cybersecurity is a strategic concern for executives, not just IT teams. Business leaders seek clear, relevant answers to questions such as “Are we protected against ransomware?” or “Do we have gaps in compliance?”
The reference architecture supports those conversations by:
- Demonstrating how current investments address specific risks.
- Highlighting areas that require further attention or budget.
- Providing a foundation for prioritizing security initiatives.
This moves the discussion from reacting to incidents to executing a planned, informed approach.
Integration: A Practical Advantage
One of Microsoft’s strengths is that its security products are designed to work together seamlessly. Defender for Endpoint, Microsoft Sentinel, Entra ID, and Purview share intelligence and automate responses without requiring custom development.
In mixed environments, integrating third-party tools can require additional investment and may not deliver the same speed or depth of response. The architecture helps organizations assess whether maintaining a fragmented environment is sensible — or if consolidating could enhance both protection and efficiency.
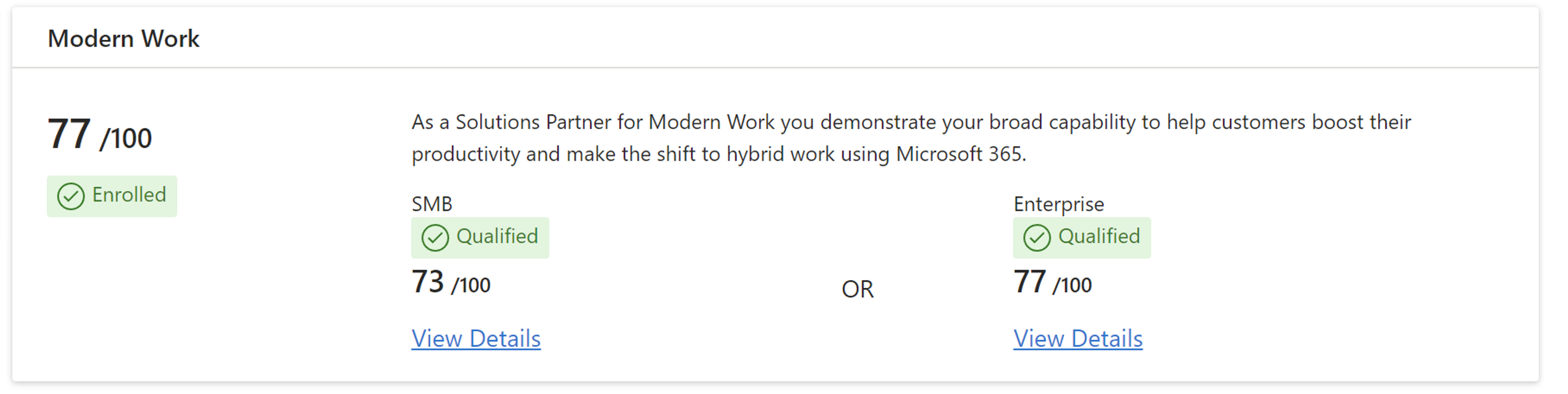
Where to Start: Secure Score and Early Wins
With so much capability on the table, deciding where to begin can be challenging. Microsoft Secure Score offers a prioritized set of recommendations to harden security across identity, endpoints, and cloud workloads. Aligning these recommendations with the reference architecture ensures that initial improvements fit into the wider roadmap and deliver measurable progress.
Extending Protection Beyond Microsoft
The architecture isn’t limited to Microsoft workloads. With Defender for Cloud Apps, organizations can monitor and control third-party SaaS platforms, including Salesforce, Dropbox, Google Workspace, and Slack.
This is particularly important in managing Shadow AI — the unsanctioned use of generative AI tools by employees. Running an assessment with Defender for Cloud Apps uncovers this usage, evaluates risk, and informs decisions on whether to block, monitor, or integrate these tools securely.
From Framework to Operations
A security plan must be more than a diagram — it has to be operational. That means:
- Tracking detection and response metrics such as Mean Time to Acknowledge (MTTA) and Mean Time to Remediate (MTTR).
- Centralizing log collection and analysis in a SIEM like Microsoft Sentinel.
- Continuously improving configurations based on lessons learned from incidents and new threat intelligence.
This approach turns the reference architecture into a living part of the organization’s security practice.
Bringing AI into the Security Stack
Threat actors already use AI — defenders need to do the same. Microsoft Security Copilot brings generative AI capabilities to security operations, allowing teams to:
- Query security data in natural language.
- Receive configuration guidance based on best practices.
- Automate aspects of investigation and response.
Linked with the architecture, Security Copilot can help teams respond faster and with greater accuracy, especially in organizations without large in-house security teams.
Turning Expertise into Opportunity
For Microsoft partners, the reference architecture is both a delivery tool and a sales enabler. It creates a natural pathway into Microsoft-funded engagements such as:
- Threat Protection Workshop
- Data Security Workshop
- Modern SecOps Workshop
Each engagement can lead to design, deployment, and managed services projects, as well as opportunities to streamline licensing and reduce redundant spend.
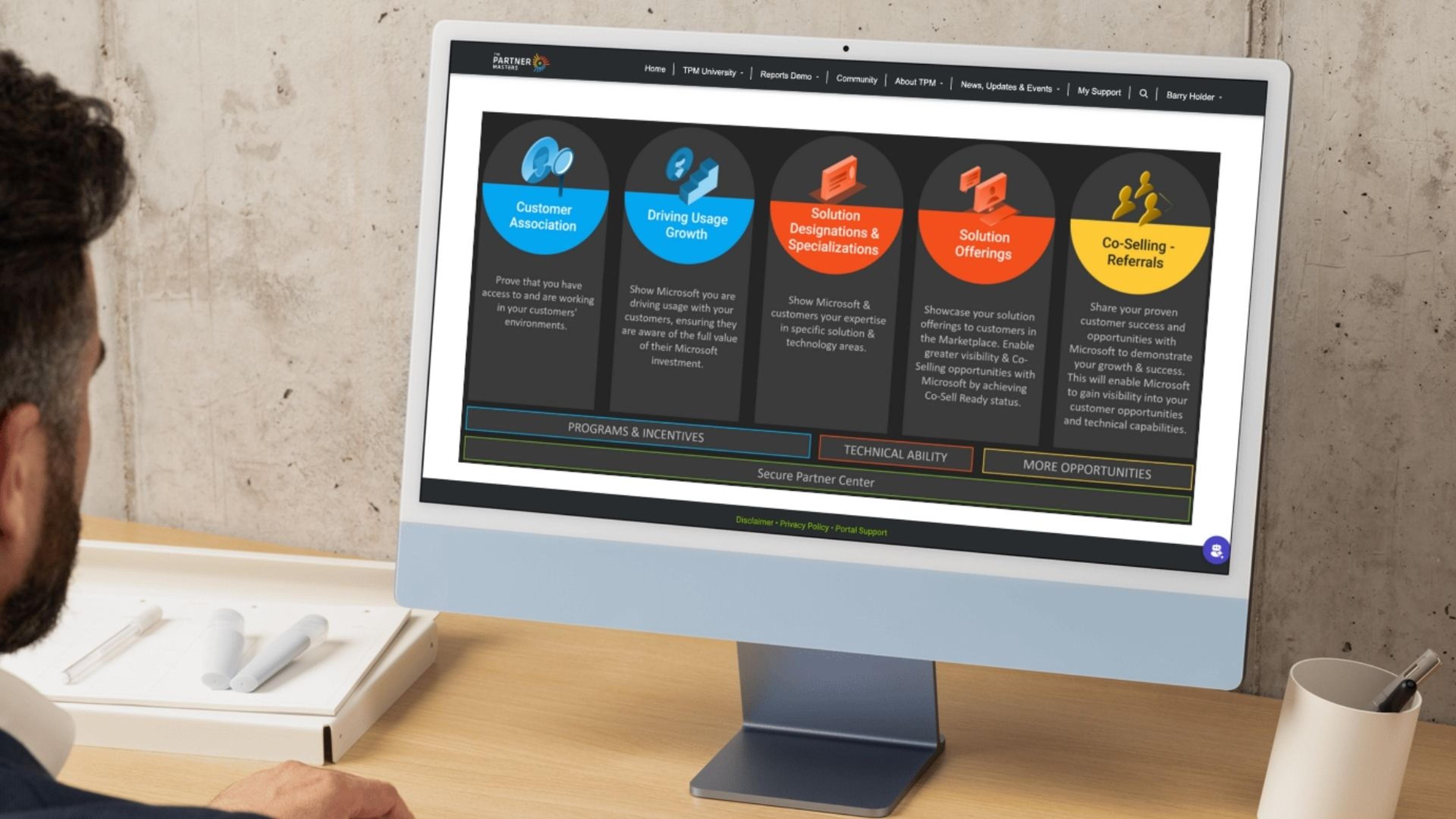
Unlock the Full Value with Partner Command Center
Within the Partner Command Center, Partner Masters provide partners with the necessary resources to implement the Microsoft Cybersecurity Reference Architecture. Members gain access to editable templates, funding program guides, and ready-to-use client materials — all designed to help lead confident conversations about security.
If you’re ready to use Microsoft’s security framework to protect customers, strengthen relationships, and grow revenue, now is the time to act.
Join the Partner Command Center today and transform the framework into a comprehensive plan for resilience, compliance, and growth.